Slides at slides
Ransome
Some Related Resources
Attack Defense Paradigm
I attack your computer based on your OS source code
I protect my computer based on your attack source code
…
Never end
Testing Frame Work $\rightarrow$ Statisitcs
OK, if system A fails at 5 different virus and system B only fails at 1, who is better? You can’t tell.
Need an index that’s independent from protection method and attack method.
- Ideal defense $\rightarrow$ no ransomware anymore
- k-lag defense, let ransomware run $k\ \micro\text{s}$ and see the destruction.
- Destruction means the unrecoverable data in mapped disk(target storage region which stores targeted files to ransomware)
Question :
How generic should this testing framework be?
Generic
Generic meeans the testing framework should be independent of variables. But what are those variables. If storage system types isn’t one of these variable, then I think the way is to widely test upon GFS, XFS, mySQL, postgreSQL …
Variable can also include the type of ransomware :
Observation
- Current ransomware are hard to work with because
- server might be off-line (Many can’t connect to server).
- only available on windows, hard to probe
- some ransomware destorys the system (ban all the system-level operation, not allowing you to probe any system-level data)
- With working ransomware, still
- hard to standardize, why choose this one over other ransomwares?
- not summable (fs lost 70% data over ransomware1, 80% data over ransomware2, another file system fs’ lost 90% data over ransomware1 50% data over ransomware2), which is better? Can we take sum over any data?
- Most of ransomwares disregard remote backups, while having access to credential manager.
Standardized ransomware
- Healthy : do nothing except for encryption data
- Transparent : can be adjusted for testing framework
- Working : can encryt data without the existence of server.
- Flexible : can do batch test.
How does storage systems do their journal?
- Many of the storage systems don’t do data journal, they do metadata journal only for performance.
- Some systems do coW, but that’s per transaction, the amount of recoverable files are limited.
Data backup
Generic way to defend against ransomware.
So need to study journal and logging behavior…
The most important problem is frequency and expiration rate of those backups, I think.
Now I think those can be omitted because index should be from “stationary” data backups and calculate their ratios.
Backup Resources
Remote backups : crisis on credential manager
The following 3 slides are from https://www.nirsoft.net/utils/credentials_file_view.html
Data Stored In Credentials Files
Windows operating system stores the following information inside Credentials files:
- Login passwords of remote computers on your LAN.
- Passwords of mail accounts on exchange server (stored by Microsoft Outlook)
- Windows Live session information.
- Remote Desktop 6 user\password information.
- Internet Explorer 7.x and 8.x: passwords of password-protected Web sites (“Basic Authentication” or “Digest Access Authentication”)
- Password of MSN Messenger / Windows Messenger accounts
Credentials File Location
You can find the Credentials files of Windows in the following locations:
C:\Users\[User Profile]\AppData\Roaming\Microsoft\Credentials (Windows Vista and later)
C:\Users\[User Profile]\AppData\Local\Microsoft\Credentials (Windows Vista and later)
C:\Windows\system32\config\systemprofile\AppData\Local\Microsoft\Credentials (Windows 8 and later)
C:\Documents and Settings\[User Profile]\Application Data\Microsoft\Credentials (Windows XP)
C:\Documents and Settings\[User Profile]\Local Settings\Application Data\Microsoft\Credentials (Windows XP)
Those are no valid locations, but I duplicated .crd file to desktop and find the encrypted results.
And there are ways to decryt those account / password
CredentialsFileView is a simple tool for Windows that decrypts and displays the passwords and other data stored inside Credentials files of Windows.
Ransomware operates at your comp. Message protection will be likely to fail.
You logged in to onedrive today, so your cached verification will bypass the text-message-verification.
Then you have a ransomware.
But in testing framework’s perspective, what are we testing against? The expiration rate of cloud service?
Are we testing subject storage system or the cloud backup sub-system?
Remote storage
summary (might expire)
Implementation
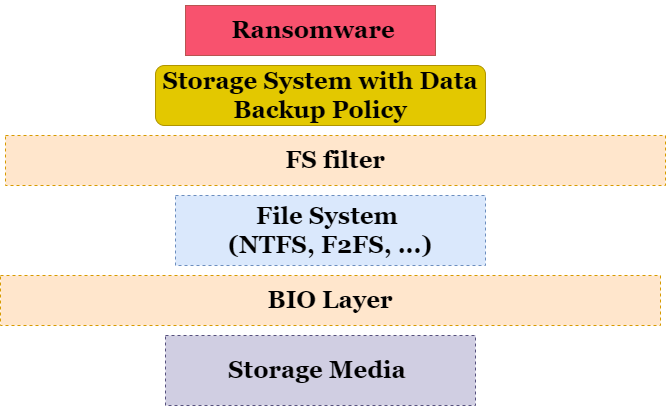
Need this tool to be portable, probably have to encapsulate the code and provide some APIs. However, the probes within BIOs should be enforced (not optional).
Ideas, now I don’t think these are going to help:
Windows & IO
- Windows7 iso
- Windows 10 ISO should be available…
Current obstacles
-
NTFS does NOT have data journal. Typical ransomwares don’t exist on linux.
- Don’t really know how to trace journals and logs(def unable to do it in block level) in Windows and with storage systems that I can’t access source code.
- Implicit problem, layering : how to trace data backups ?
-
Might need to build a standardized ransomware(may need to study the repos on github a little bit)
- False positive : it happens to many Filesystem Filters based detecting tools.
Current obstacles (cont.)
-
More comments on false positive : it also suggests a software-subjected detection is worse than system-subjected detection.
-
I don’t think logal backups have any meaning because backups essentially are files.
-
If local backups failed all the time, then aren’t we just testing the cloud service’s security. a.k.a. how likely it can be accessed by ransomware?
Update : Design and New thinking (2023-05-04)
Several things mentioned in the meeting
- We need to target several storage systems, the only thing we need to care about is the data backups.
- Most of the targeted systems only have one copy of data (e.g. NTFS only logs metadata)
- So we need to simulate remote backups
- We can be real by using One Drive API & video & Google Cloud API
- Or we can fake it so that our testing framework does NOT have that many dependencies
- Testing framework needs to utilize several core features of ransomwares.
- To do that we need to analyze the behaviors of ransomwares (existing)
- We can adjust assumptions on
- ransomware privilege level
- storage backup time (meaning at those time the back-up storage is connected to OS)
- back-up frequency (we have backup)
Mini filter, our solution to NTFS
ACL problem
Solution to “Discrete” statistics
What if the backups are either all-encrypted or all-safe.
Divide into two aspectes
-
Security
-
Consistency
Notes on security
In data backup industry, security usually means how safe the remote server is, that is, even when malware has external access to the server, how safe your data is.
They typically do it via data encryption.
Note that this is no longer valid to ransomware because ransomware can have the same access right as normal user
Log-strcutred FS : Natural Killer of Ransomware
- I can use GC attack to clear your logs
More notes on GC : F2FS
This policy selects a victim section not only based on its utilization but also its “age”. F2FS infers the age of a section by averaging the age of segments in the section, which, in turn, can be obtained from their last modification time recorded in SIT. With the cost-benefit policy, F2FS gets another chance to separate hot and cold data.
Bonus : IPLFS
https://www.usenix.org/conference/atc22/presentation/kim-juwon
&
How to center the image in marp
Current Structure of Our Testing Framework
Ransomware Report and Key Characteristics
and deleting the shadow copy of user fles
According to (Kharraz et al. 2016) there are three ways ransomware encrypts fles: (i) overwriting originals iginals, and (iii) encryption and secure deletion of the originals
rm calls unlink. They have slight difference but for testing system, they are basically the same.
Tracing
blktrace, blkparse, btt
sudo apt-get install blktrace
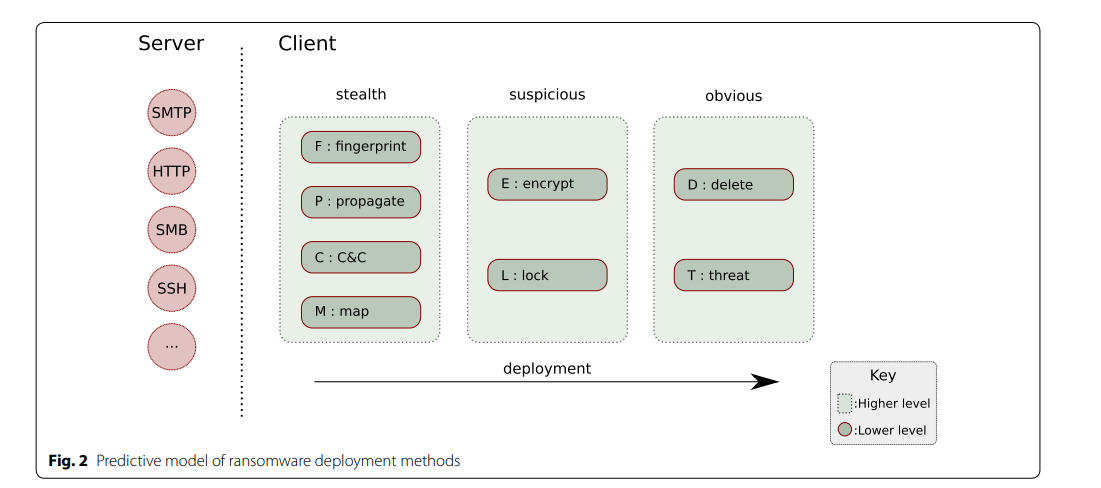
Mapping from Ransomware Set to Standardized Ransomware
- Need to show ransomware can be mapped to a certain group of characteristics
- Many characteristics about ransomware are encryption related, so it’s not related to target system
- So the only sets of characteristics should be :
Propagate
Might need to check AFS, NFS, and more sharing related storage systems to check if the webservice network is secure enough.
NFS
main page server client setup(Quick) tutorial
Ext4 Mapping problem

Email : haor2@illinois.edu
Website : http://moomoohorse.com